Delivery | HackTheBox

As like always let’s start with some reconnaissance using nmap. Here :
Machine IP: 10.10.10.222
nmap -A -p- -T4 -v -oN Nmap.txt 10.10.10.222Important Output
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2
80/tcp open http nginx 1.14.2
8065/tcp open unknownExploring port 80
On http://10.10.10.222:80 we are greeted with a landing page

When we look into the page source we find that the domain should be delivery.htb [As happening with almost all the challenged on HTB].

So, let’s add it to the /etc/hosts. The updated /etc/hosts should look like:

Now on visiting : http://helpdesk.delivery.htb/ we are treated with a ticketing system.

Let’s go back and analyze http://delivery.htb/ we see a Contact Us link also http://delivery.htb/#contact-us which may be giving us a hint for the process.

And this MatterMost server is opening at http://delivery.htb:8065/login

With some googling
“Mattermost is an open-source, self-hostable online chat service with file sharing, search, and integrations. It is designed as an internal chat for organisations and companies, and mostly markets itself as an open-source alternative to Slack and Microsoft Teams”
So it looks like first we need to get the Email-id from http://helpdesk.delivery.htb/ and then login at http://delivery.htb:8065/login
So let’s register for a new account on http://helpdesk.delivery.htb/account.php?do=create But on creating it’s not working. But it looks like we can open a ticket http://helpdesk.delivery.htb/open.php

On creating the ticket we receive the confirmation

So great we got a mail ID now and now we looking for password :).let’s visit : http://delivery.htb:8065/signup_email and create it with the @delivery.htb email we are allocated with.

Now it says that a confirmation mail is sent to the email address provided. Now we can access the emails on our @delivery.htb from http://helpdesk.delivery.htb/view.php

and yes we received the mail from mattermost :) Bingo

On opening the link we got the verification for mattermost and we can login now.

So on logging in we are directed to go to internal where we find an announcement which exposes creds for osTicket Agent

With these creds :) I wen’t on for a rabbit hole and wasted time on OsTicket. These creds will easily land you on system using ssh and you can read the users.txt
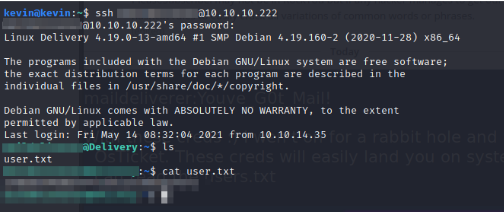
Our user has no superpowers :’) need to get rid of him. On looking for configuration file
find / -type f -name config* 2>/dev/nullWe get a json file at /path_to_file/config.json and we can see creds for mysql

So let’s login to mysql as this user
mysql -u username -p passwordNow seeing the databases: show databases;

To set a database: use databasename;
Now to see tables: show tables;

Now dumping data of root user: select * from <tablename> where Username=’root’;
It actually dumps a hash for us : select password from <tablename> where Username=’root’;
Let’s bring it to our local machine and try to decrypt it :)
So it’s time to use hashcat
According to hashid it says that it’s bcrypt

Now if we go back to the point when we logged in to mattermost

We see that a pass-phrase has been mentioned and it’s been asked to refrain from using variant of that pass phrase.
Let’s create a file `word.txt` with the phrase and use best64.rule to create 64 variants of that pass phrase. Make sure to enter the correct pass-phrase as I wasted a long time due to a typo :’)
hashcat -r /usr/share/hashcat/rules/best64.rule --stdout word.txt > password.txtNow let’s create `hash.hash` to store our hash we received from mysql and bruteforce it against the generated password list.
hashcat -m 3200 hash.hash password.txtIt gives us the password for root user for mattermost but as it’s mentioned(in mattermost chats) that password has been reused manu time we tried our luck on root user with “su - root” and it worked.

Learnings
- Always read read ……………
- hack breath think ask hack
- Look for config files
- Creating variants of passphrase using best64 rule
- Try not to do typo :’)
- Cracking bcrypt
Will come-up with a new writeup soon till then happy hacking people.